DDoS Attacks Demystified: Understanding the Threat and Mitigation Strategies
In today’s interconnected world, cyber threats loom large, and among them, Distributed Denial-of-Service (DDoS) attacks stand out as a persistent and damaging threat. These attacks can cripple websites, online services, and even entire networks, disrupting businesses, causing financial losses, and eroding trust among users. Understanding the mechanics, motives, and mitigations of DDoS attacks is crucial for any organization serious about protecting its digital assets.
Contents
What is a Distributed Denial-of-Service attack?
It is a malicious attempt to disrupt the normal traffic of a targeted server, service, or network by overwhelming it with a flood of internet traffic. Unlike traditional Denial-of-Service (DoS) attacks, which are carried out using a single source, DDoS attacks leverage multiple sources, making them more powerful and harder to mitigate.
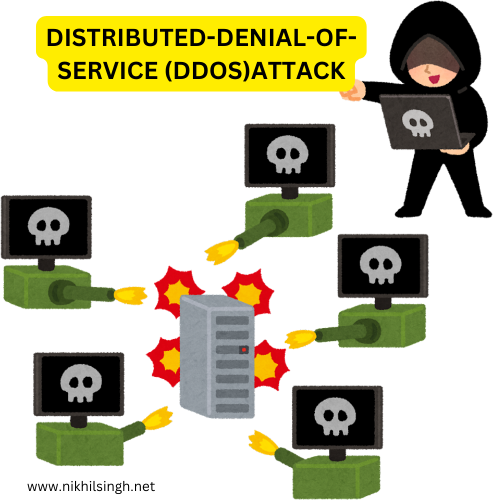
How does a Distributed Denial-of-Service attack work?
A DDoS attack typically involves three main components: the attacker, the command-and-control (C2) infrastructure, and the compromised devices, often referred to as bots or zombies. These bots are usually ordinary computers, smartphones, or IoT devices that have been infected with malware, allowing the attacker to control them remotely.
The attacker commands these bots to flood the target with a huge volume of traffic, overwhelming its capacity to handle legitimate requests. This flood of traffic consumes the target’s bandwidth, processing power, or other resources, effectively denying service to legitimate users.
Motives Behind Distributed Denial-of-Service Attack
It can be motivated by various factors, including financial gain, political activism, revenge, or simply the desire to cause chaos. For example, attackers may launch DDoS attacks against online businesses to extort money in exchange for stopping the attack (known as ransom DDoS), or they may target government websites to protest against specific policies.
Types of Distributed Denial-of-Service Attack
There are several types of DDoS attacks, each with its own characteristics and impact. Some common types include:
- Volumetric Attacks: These attacks flood the target with a high volume of traffic, aiming to exhaust its bandwidth. Examples include UDP floods and ICMP floods.
- Protocol Attacks: These attacks exploit vulnerabilities in network protocols to overwhelm the target’s resources. Examples include SYN floods and Ping of Death attacks.
- Application Layer Attacks: These attacks target the application layer of the OSI model, aiming to exhaust the target’s resources at the application level. Examples include HTTP floods and Slowloris attacks.
Mitigating DDoS Attacks
Mitigating DDoS attacks requires a multi-layered approach that combines proactive measures with reactive strategies. Some common mitigation techniques include:
- Firewalls and Intrusion Prevention Systems (IPS): These can help filter out malicious traffic before it reaches the target.
- Content Delivery Networks (CDNs): CDNs can absorb and distribute traffic across multiple servers, reducing the impact of an attack.
- Rate Limiting: By limiting the rate at which requests are processed, organizations can mitigate the impact of DDoS attacks.
- Anomaly Detection: Monitoring network traffic for unusual patterns can help identify and mitigate DDoS attacks in real-time.
- Cloud-Based DDoS Protection Services: These services can provide scalable protection against DDoS attacks by leveraging cloud resources to absorb malicious traffic.
Conclusion
In conclusion, Distributed Denial-of-Service attack is a serious threat to organizations of all sizes, targeting their digital infrastructure and disrupting their operations. Understanding the nature of DDoS attacks, their motives, and the techniques used to mitigate them is essential for organizations seeking to protect themselves against this ever-evolving threat. By implementing robust security measures and staying vigilant, organizations can minimize the risk of falling victim to DDoS attacks and ensure the uninterrupted availability of their online services.
Also, read SQL Injection Attack : The Silent Assassin
Follow the official LinkedIn profile for more future updates, Nikhil Singh.